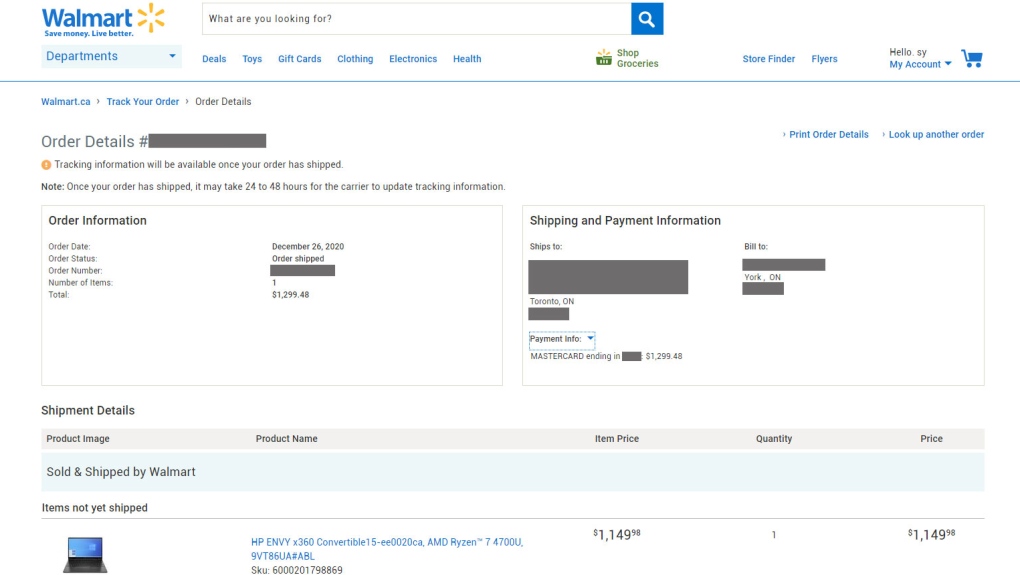
TORONTO -- Customers’ names, shipping and billing addresses, order dates, methods of payment and the last four digits of the credit cards used were on full display for orders of a $1,500 laptop computer in Ontario, a $700 spin bike in Saskatchewan, and more than $1,100 worth of baby gear in B.C.
These are just a few samples of Walmart.ca orders CTVNews.ca was able to call up on the retailer’s website Tuesday that demonstrated the ease with which customer information could be accidentally exposed.
Sanjay Bhatia said he was looking up his Walmart.ca orders to return one of the items when he stumbled across what one security expert described as a “highly sensitive” data exposure flaw in the company’s online ordering and tracking system.
“(It’s a) huge exploit. And I’m just flabbergasted. I'm actually pissed off because, you know, my stuff was on there too,” said Bhatia, who works in IT himself. He said efforts to contact Walmart Canada about the issue were unsuccessful, which was when he decided to reach out to CTVNews.ca.
“Nobody really wants their stuff to be out there like that. I would figure, a company like Walmart -- like, come on.”
Bhatia explained how he was able to access information and orders belonging to other customers through the general web page https://www.walmart.ca/order-lookup when logged into his own Walmart.ca account. CTVNews.ca was able to effortlessly replicate those steps and call up numerous customer orders -- potentially hundreds -- across the country, but is excluding details of how these customer accounts were accessed out of an abundance of caution. Similar steps were tried on Amazon.ca, with no sensitive information getting exposed.
The information exposed on Walmart.ca included full customer names, billing addresses, whether the product was being delivered to a home address or a Walmart location for in-store pick up. CTVNews.ca could also see if the order was paid with a Visa, Mastercard, Amex, or PayPal.
The web page through which the personal information could be accessed has since been redirected to a “Contact Us” page for online shopping, after CTVNews.ca reached out to Walmart Canada and brought the issue to the retailer’s attention.
But Bhatia found that customer information could still be accessed via another related web page on Walmart.ca, a step that CTVNews.ca was able to replicate as well. That page was also eventually disabled and redirected to the same online shopping contact page after Walmart Canada was informed that another link had the same issue.
“We take customer privacy very seriously and have numerous security protocols in place to protect it,” spokesperson Adam Grachnik said in an email statement.
“As soon as this came to our attention today, and out of an abundance of caution, we immediately disabled the webpage where guest customers could access their order tracking details. We are looking into the matter further.”
A COMMON SECURITY FLAW
“In this case, I think it would constitute a highly sensitive example of data exposure,” said cybersecurity expert Yuan Stevens in a phone interview.
Even so, Stevens, the policy lead on technology, cybersecurity and democracy at the Ryerson Leadership Lab and the Cybersecure Policy Exchange, said this was not entirely unusual or surprising. She noted that this type of flaw was on the Open Web Application Security Project’s (OWASP) 2017 top 10 list of common website security risks.
Stevens, who is also an expert on bug bounty programs -- where companies incentivize people to find flaws in their system -- noted that Walmart does not incentivize hackers to look for flaws despite having a “responsible disclosure policy”. This is a program that allows ethical hackers to alert a company of any security vulnerabilities they may find on their website.
Walmart's policy states a person "may be eligible for monetary compensation" at Walmart's discretion. By comparison, Amazon's incentives are clearly laid out, with payments ranging from $100 to $15,000 depending on the severity of the vulnerability found.
When someone found a flaw on Walmart’s Mexico website in 2017, it took the company six months to fix it, according to openbugbounty.org. The average time for Amazon to respond and resolve issues was 22 days, according to figures from Hackerone, a company that serves as an intermediary between companies and hackers who find flaws.
Walmart did not immediately respond to CTVNews.ca’s questions about the security flaw found in 2017 or questions about its responsible disclosure policy.
“The fact that the company took six months to patch a flaw is definitely a data point that hackers will look at and say, ‘Well, if they're going to take so long to patch, like, it's not really worth my time to deal with that.’ And the fact that people aren't incentivized to find flaws on their website as well,” Stevens said.
On immuniweb.com, which does automated web application security testing, Walmart.ca was given a B, or a score between 60 and 69, which Stevens says is “not great”.
“What I was able to glean from this … is that there are definitely flags like misconfigurations or weakness even demonstrated from this very simple AI-powered analysis of a website....it shows how easy it is for Walmart to know how insecure their website is.”
By comparison, Amazon.ca, got an A, or a score between 90 and 99.
Stevens said if there are multiple weaknesses on a website, hackers can connect flaws or “chain” them to create greater risks for the company or users of the website. These risks can include identity fraud, doxxing, an individual’s physical, psychological safety or financial security.
“The worst case scenarios here are what gives me cause for concern,” she said.
Bhatia, the customer who initially flagged the issue, said it would be easy for someone to write a program to cull the unsecured information.
“Because I’m an IT guy, I can write a script, literally on my Red Hat Linux box and just go and grab everything … to see everybody’s name, address, and credit card information,” said Bhatia, adding that there are also ways to find out the missing credit card numbers.
Walmart also has obligations under the Personal Information Protection and Electronic Documents Act (PIPEDA) in circumstances where there is a real risk of significant harm, like identity theft, Stevens said.
“These are actually really simple flaws. In this case, it sounds like an average person can take advantage of this … it means that Walmart has not tested the security of their website and hasn’t prioritized security.”
“It’s really important for Walmart to take this seriously not only because of what is obligated of them … but because of the risk it poses to a customer,” Stevens said.
Edited by CTVNews.ca producer Sonja Puzic